Contents:
1. Overview – MuddyWater Operations on Israel Infra
Overview – MuddyWater Operations on Israel Infra

Since October 7, 2024, MuddyWater has significantly ramped up its cyber operations targeting organizations in Israel. This surge in activity is part of a broader campaign that involves deploying a new custom malware implant called BugSleep. This backdoor allows MuddyWater to execute remote commands and transfer files on compromised systems, marking a shift from their previous use of legitimate remote management tools like Atera Agent and Screen Connect.
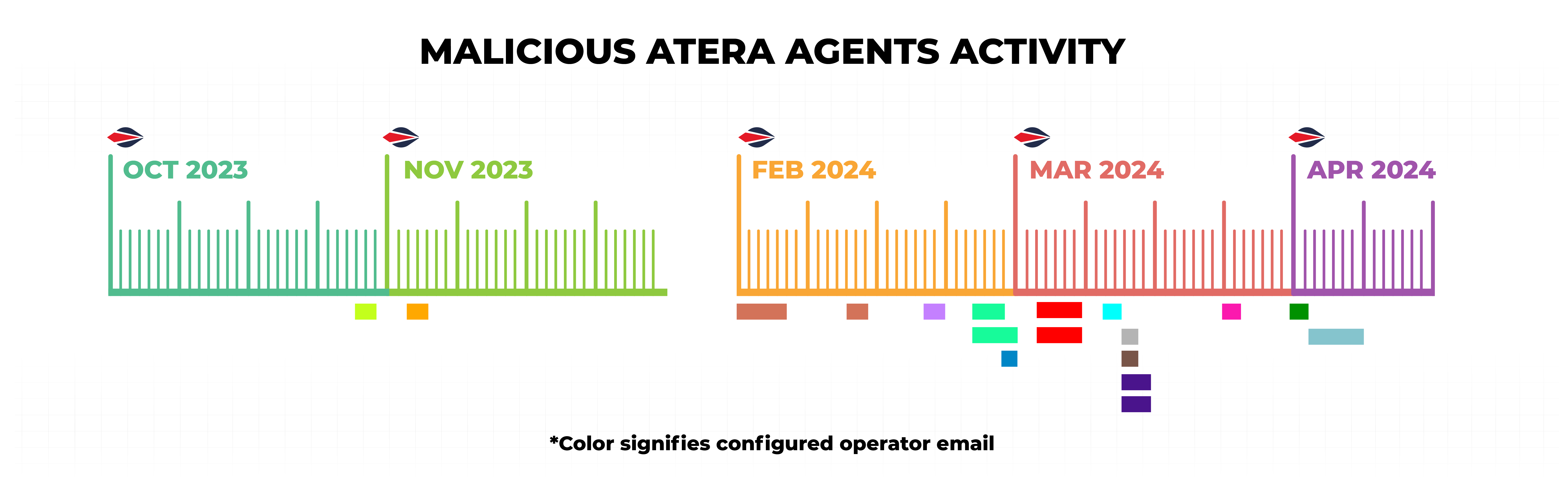
Figure II Estimated timeline of Atera agent activity
MuddyWater's attacks in Israel have primarily utilized phishing emails disguised as invitations to webinars or online courses. These emails lead recipients to download archives containing malicious payloads hosted on the Egnyte secure file-sharing platform or similar. The phishing lures have evolved to include generic-themed content, such as PDF files embedded with malicious links, allowing the group to reuse the same lure across different targets and regions.
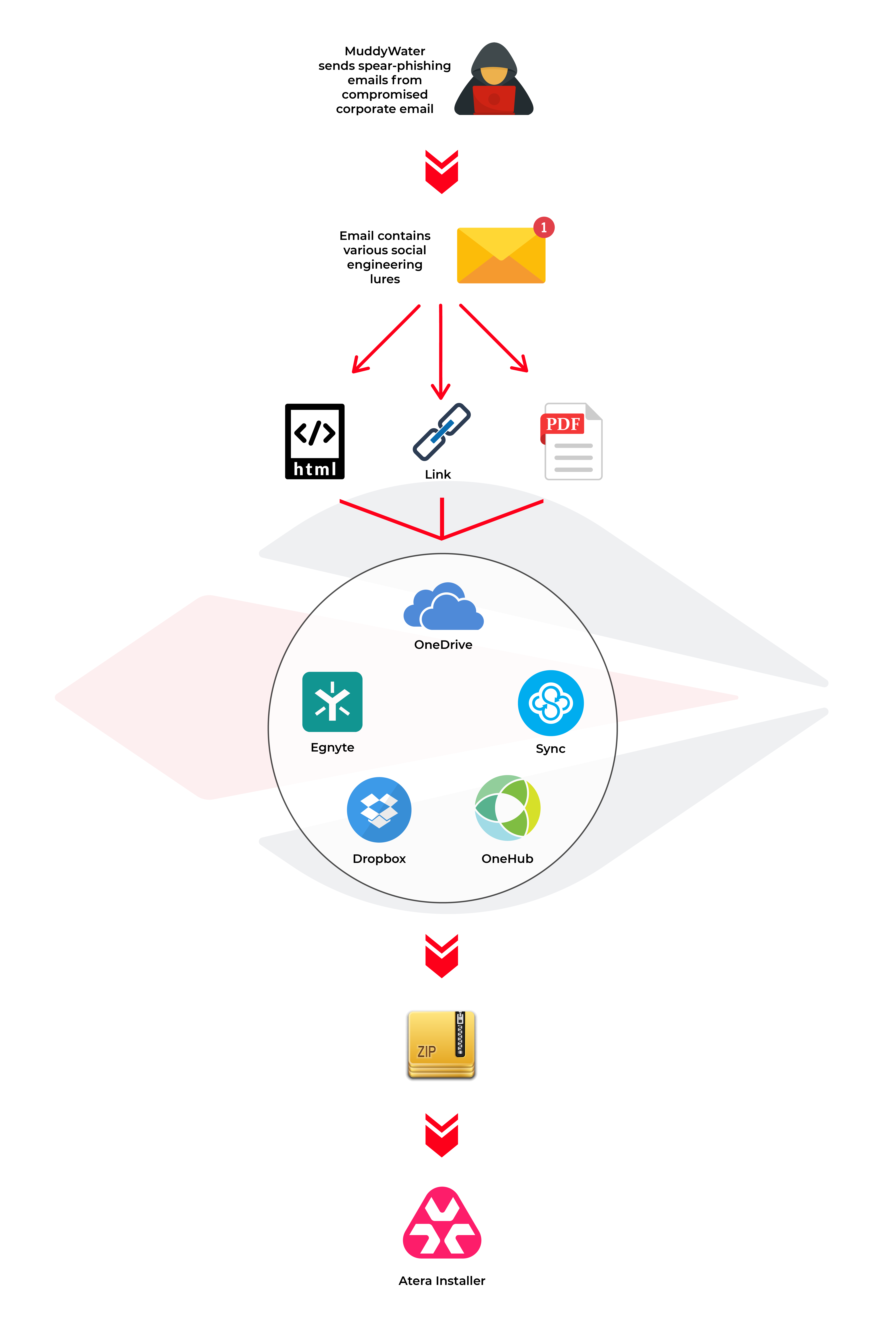
Figure III MuddyWater campaign overview.
The primary targets of these campaigns in Israel include government entities, municipalities, media outlets, and travel agencies. The persistent nature of these attacks reflects MuddyWater's strategic interest in Israeli targets, with a notable increase in the volume and sophistication of their operations in the region since the start of the Israel-Hamas war in October 2023 (Check Point Research) (The Record from Recorded Future).
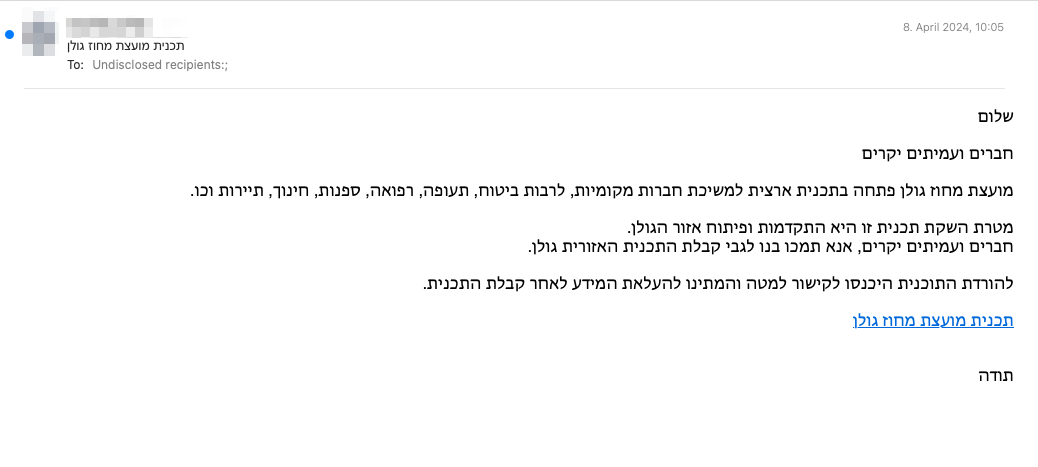
Figure V 2024 spear phishing email linking to Atera Agent, hosted through "Egnyte" file sharing
The introduction of BugSleep and the continuous improvement of its functionality indicate that MuddyWater is actively refining its tools and tactics to evade detection and enhance their cyber-espionage capabilities. The group's focus on Israel underscores their ongoing efforts to infiltrate and compromise critical sectors within the country.
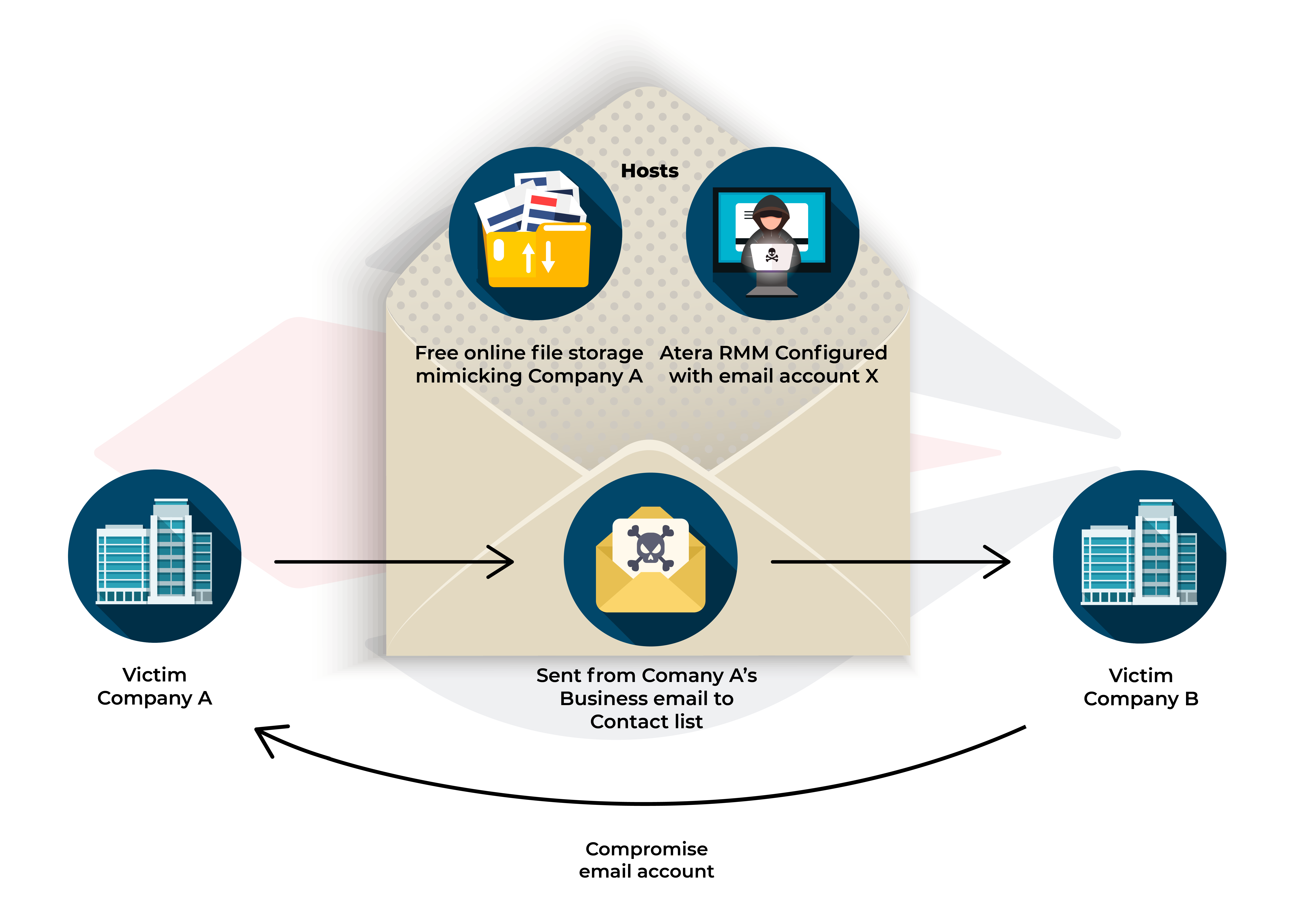
Figure VI Documented spreading technique
Before the introduction of BugSleep, MuddyWater extensively utilized Atera Agent as part of their toolkit to maintain persistence within targeted networks. Atera Agent, a legitimate RMM tool, provides comprehensive remote access capabilities, making it an attractive option for cyber attackers aiming to control and monitor infected systems discreetly.
Misuse of Egnyte:
Egnyte, a legitimate file-sharing platform, has been exploited by MuddyWater. The attackers align Egnyte subdomains with the company names used in their phishing emails. When the shared link is opened, recipients see the sender’s name, which appears legitimate and matches local naming conventions.
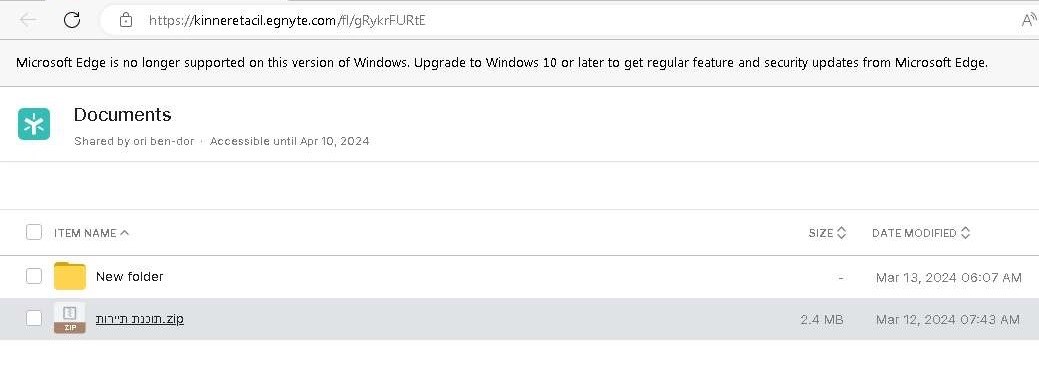
Figure VII Custom Egnyte folder
Technical Details of MuddyWater's Use of Atera Agent
Deployment and Installation:
- Initial Access: MuddyWater often gains initial access through phishing emails, exploitation of vulnerabilities, or other means. Once inside the network, they deploy the Atera Agent to establish a foothold.
Figure VIII Spear phishing email from April 2024 linking to Atera Agent, hosted via "Egnyte" file sharing
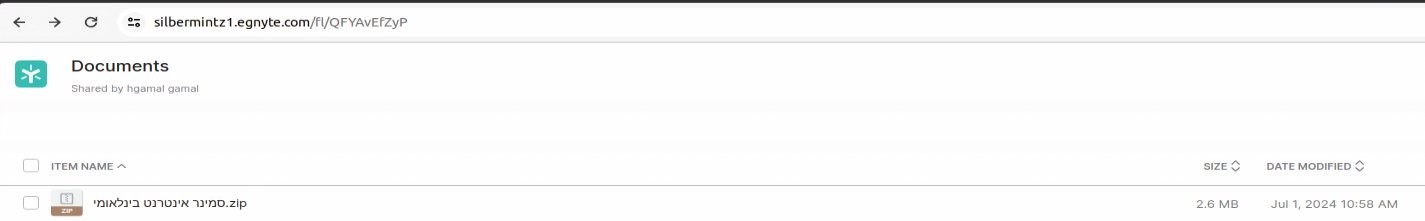
Figure IX Custom Egnyte folder
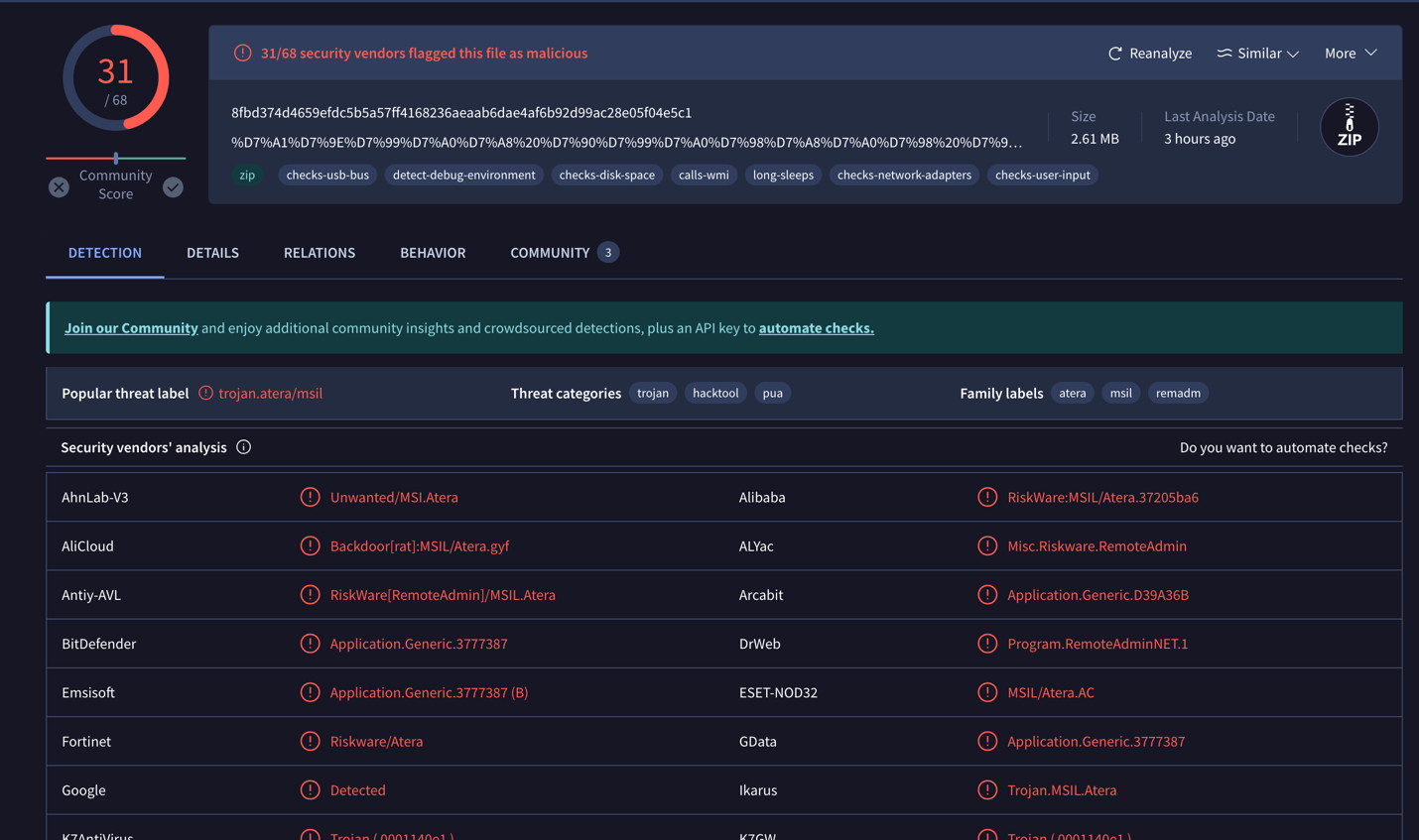
Figure X Virus total lookup of the Archive file
Configuration and Use:
- Agent Configuration: MuddyWater customizes the Atera Agent to bypass security measures. This includes altering the agent’s configuration settings to avoid detection by security tools and to blend in with legitimate network traffic.
- Command and Control (C2): The Atera Agent is used to create a persistent connection with the threat actors. It enables them to execute commands, manage files, and perform other administrative tasks remotely. They can configure the agent to communicate with their own C2 servers using encrypted channels to obfuscate their activities.
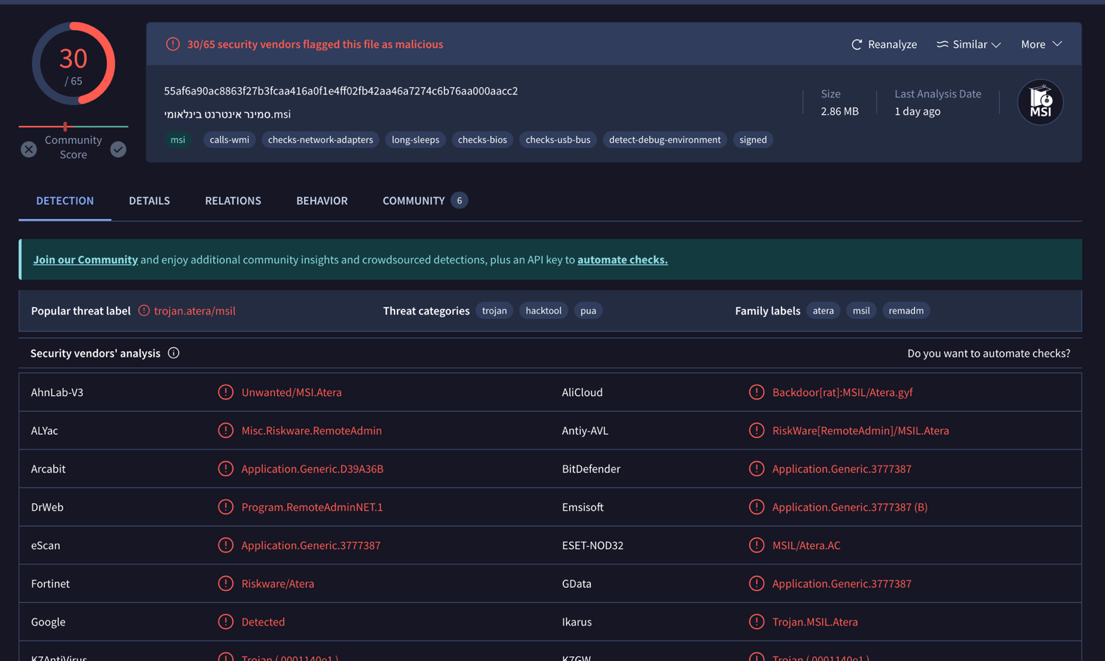
Figure XI Virus total lookup of the Atera agent
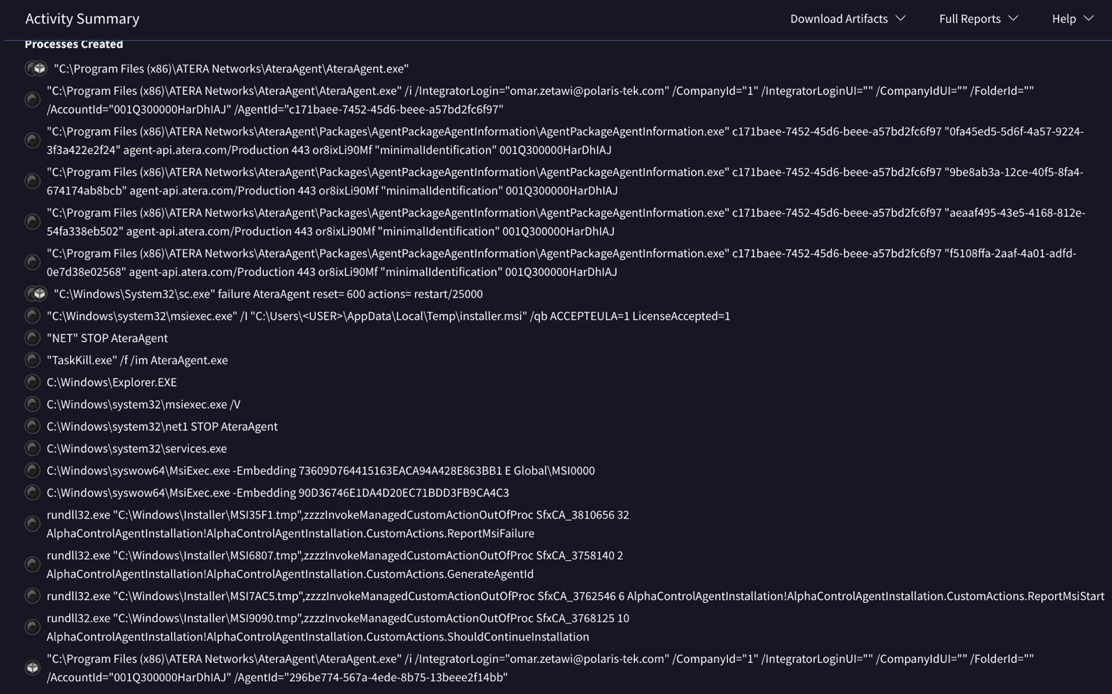
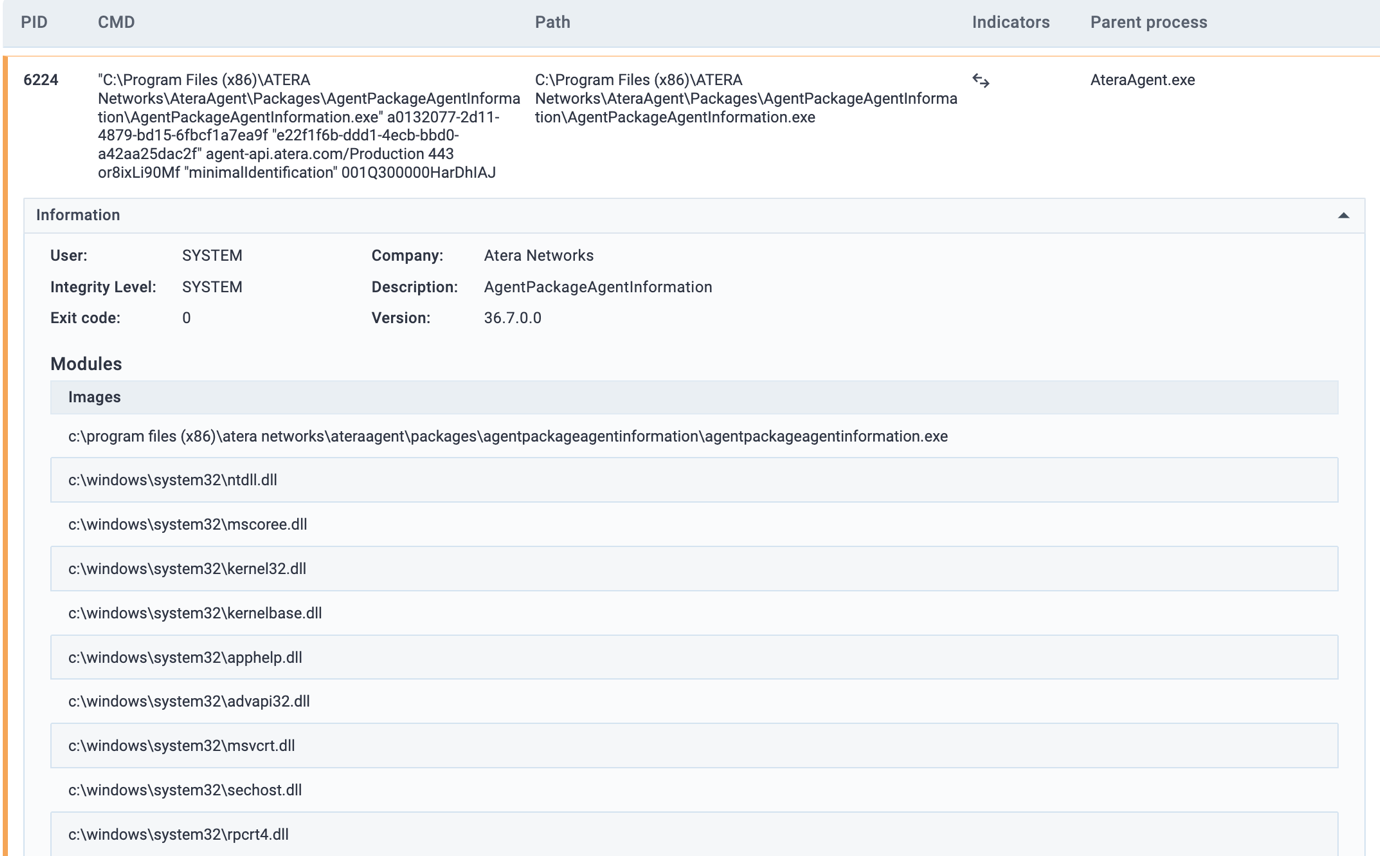
Figure XII Atera agent processes activity
Tactical Operations:
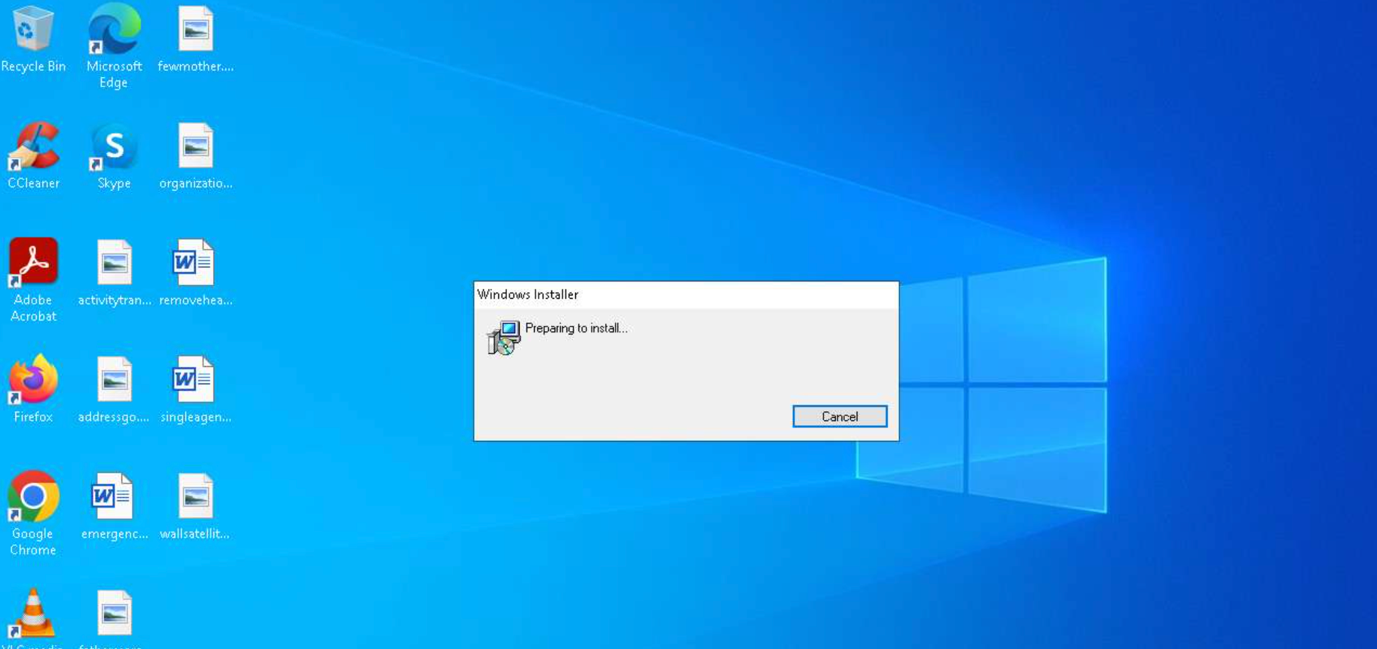
Figure XIII Installing Malicious Atera Agent
- Data Exfiltration: By using Atera, MuddyWater can access sensitive files and data on compromised systems. They might use the agent to copy, modify, or delete data, or to exfiltrate it to their own servers.
- Privilege Escalation: The Atera Agent allows them to perform privilege escalation actions, leveraging its capabilities to gain higher levels of access within the network.
- Lateral Movement: The agent facilitates lateral movement within the network, enabling the threat group to expand their access and control over multiple system
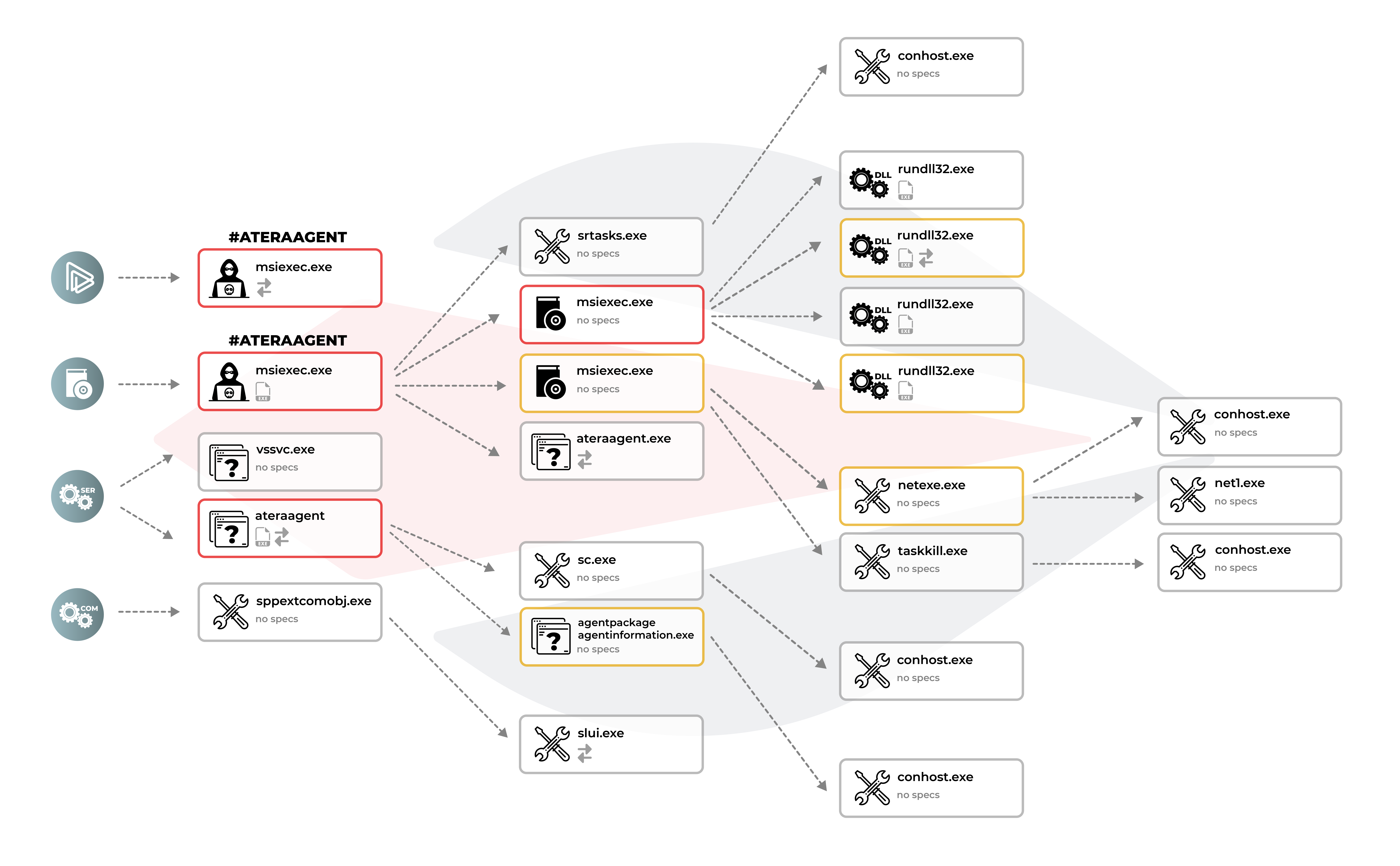
Figure XIV Behavior Graph
Persistence Using Service Control (SC):
- SC Command: To maintain persistence, MuddyWater uses the sc command (Service Control) to create or modify Windows services that execute the Atera Agent. This involves setting up services to automatically start the agent on system boot or user logon.
- Service Configuration: The group configures the service to run with appropriate privileges, ensuring it has the necessary access to maintain control over the system. The service might be disguised with names like legitimate system services to avoid detection.
- Service Modification: They might also alter existing services to launch the Atera Agent, thereby minimizing the need for new service creation and reducing the chance of detection.
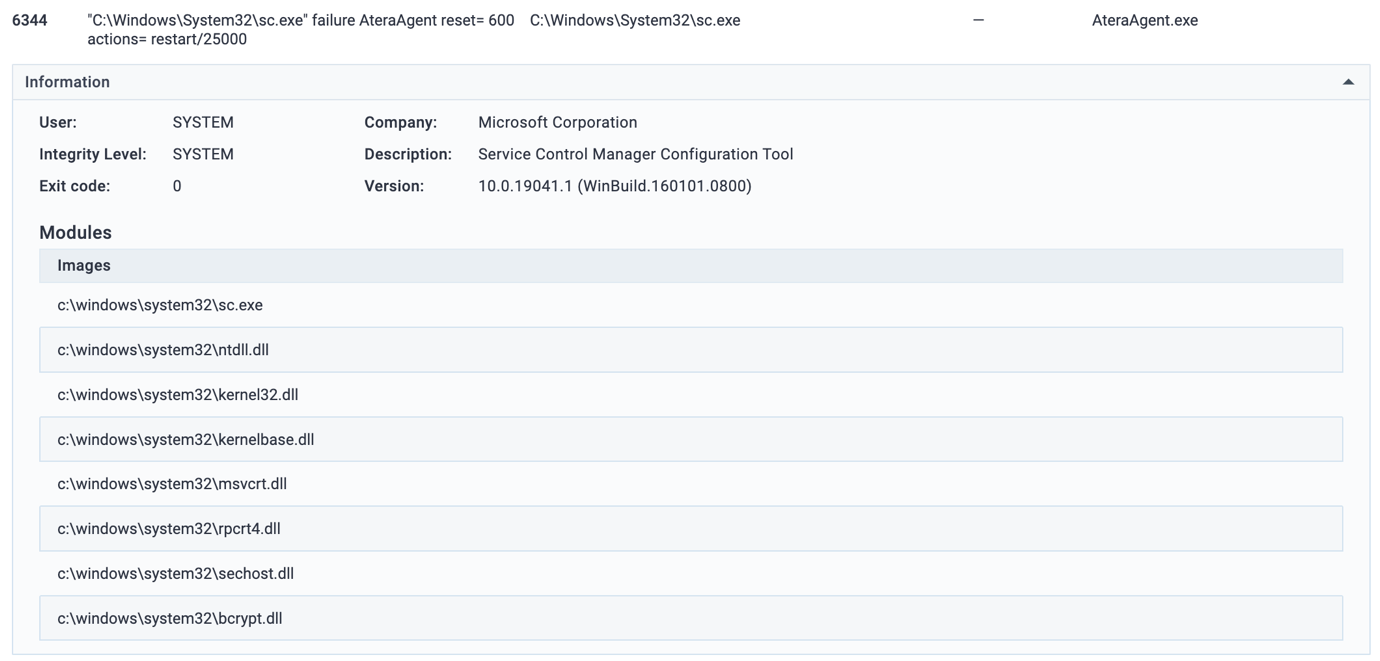
Figure XV Created AteraAgent Service
Evasion Techniques:
- Legitimate Tool Usage: Since Atera is a legitimate tool used for remote management, its presence on the network might not raise immediate suspicion. MuddyWater uses this to avoid detection by blending their activities with legitimate administrative functions.
- Modification and Masking: The group might modify the Atera Agent’s executable or configuration to avoid detection by antivirus solutions or endpoint detection and response (EDR) systems. This could involve changing file names, paths, or using encryption to hide communications.
- Service Name Obfuscation: The services created or modified for persistence might use names that resemble legitimate system services to avoid suspicion.
Figure XVI Atera Agent Process Activity
Detection and Mitigation:
- Behavioral Analysis: To detect the misuse of tools like Atera, it’s crucial to perform behavioral analysis. This includes monitoring unusual network traffic, command execution patterns, and data movement that deviates from normal operations.
- Endpoint Monitoring: Implementing advanced endpoint detection and response solutions that can recognize anomalies associated with remote management tools and unauthorized service modifications is essential. This includes monitoring for unauthorized changes, unusual administrative activities, and the creation or modification of services.
Conclusion
MuddyWater's latest campaigns illustrate a shift towards more sophisticated and covert techniques, leveraging legitimate software and supply chain trust to infiltrate and maintain access to critical infrastructure. These methods not only increase the effectiveness of their operations but also reduce the likelihood of detection, allowing them to achieve their objectives with greater efficiency and stealth.
|
MITRE ATT&CK ID |
Technique |
Description |
|
T1078 |
Valid Accounts |
Use of compromised credentials to access Atera Agent and other systems. |
|
T1566.001 |
Phishing: Spear Phishing Attachment |
Spear phishing emails with malicious attachments or links to deploy the Atera Agent. |
|
T1105 |
Ingress Tool Transfer |
Transferring Atera Agent or other malicious tools to compromised systems. |
|
T1219 |
Remote Access Software |
Use of Atera Agent for remote access and control of compromised systems. |
|
T1071.001 |
Application Layer Protocol: Web Protocols |
Using web protocols for command and control (C2) communications through Atera Agent. |
|
T1027 |
Obfuscated Files or Information |
Obfuscating the Atera Agent installation and operation to avoid detection. |
|
T1083 |
File and Directory Discovery |
Using Atera Agent to explore file systems and directories on compromised systems. |
|
T1070.004 |
Indicator Removal on Host: File Deletion |
Deleting files to remove traces of Atera Agent installation and activity. |
|
T1049 |
System Network Connections Discovery |
Gathering information about network connections through Atera Agent. |
|
T1057 |
Process Discovery |
Identifying running processes on compromised systems using Atera Agent. |
|
T1070.006 |
Indicator Removal on Host: Timestomp |
Modifying file timestamps to hide the presence of the Atera Agent. |
|
T1110.001 |
Brute Force: Password Guessing |
Attempting to brute force email accounts to gain access and deploy phishing attacks. |
Recommendations
Incident Response Recommendations
Addressing advanced cyber threats, such as those from the MuddyWater group, necessitates the expertise of the HackersEye Emergency Response Team. This dedicated team is proficient in investigating phishing campaigns and remote management tools like Atera Agent, making them essential for identifying, containing, and eliminating hidden threats. Their ability to conduct thorough forensic analysis provides a comprehensive understanding of an attack's scope, which is crucial for effective remediation.
The HackersEye Emergency Response Team is equipped with advanced tools and methodologies for detecting, containing, and eradicating threats. Their swift and decisive actions are vital for protecting critical assets, and their specialized expertise is indispensable in managing and mitigating complex cyber incidents.
With a skilled Emergency Response Team, HackersEye ensures robust defense against persistent and sophisticated cyber threats like those posed by MuddyWater.
Implement Zero Trust Architecture
- Continuous Verification: Ensure that all access requests, regardless of their origin, are continuously verified. Use multi-factor authentication (MFA) and context-based access controls.
- Least Privilege: Grant access to resources based only on what is necessary for an employee's role, reducing potential attack vectors.
Enhance Email Security
- Advanced Email Filtering: Use advanced email filtering solutions to detect and block phishing attempts and malicious attachments.
- Regular Security Awareness Training: Conduct frequent training sessions to educate employees on recognizing and reporting phishing attempts and social engineering attacks.
Monitor and Secure Remote Access Tools
- Legitimate Software Control: Regularly review and monitor the use of legitimate remote access tools (like Atera Agent) within your network.
- Behavioral Analysis: Implement behavioral analytics to detect unusual activities that might indicate misuse of legitimate tools.
Indicators of Compromise:
Domains:
|
airpaz.egnyte[.]com |
|
airpazfly.egnyte[.]com |
|
airpazflys.egnyte[.]com |
|
alkan.egnyte[.]com |
|
alltrans.egnyte[.]com |
|
bgu.egnyte[.]com |
|
cairoairport.egnyte[.]com |
|
cnsmportal.egnyte[.]com |
|
downloadfile.egnyte[.]com |
|
fbcsoft.egnyte[.]com |
|
filecloud.egnyte[.]com |
|
fileuploadcloud.egnyte[.]com |
|
gcare.egnyte[.]com |
|
getter.egnyte[.]com |
|
kinneretacil.egnyte[.]com |
|
ksa1.egnyte[.]com |
|
megolan.egnyte[.]com |
|
nour.egnyte[.]com |
|
rimonnet.egnyte[.]com |
|
salary.egnyte[.]com |
|
silbermintz1.egnyte[.]com |
|
smartcloudcompany[.]com |
|
smtpcloudapp[.]com |
|
softwarehosts[.]com |
|
onlinemailerservices[.]com |
IP Addresses:
|
5.252.23[.]52 |
|
85.239.61[.]97 |
|
91.235.234[.]202 |
|
95.164.32[.]69 |
|
146.19.143[.]14 |
|
193.109.120[.]59 |
|
194.4.50[.]133 |
Hashes:
RMM MSI:
|
20aaeac4dbea89b50d011e9becdf51afc1a1a1f254a5f494b80c108fd3c7f61a |
|
39da7cc7c627ea4c46f75bcec79e5669236e6b43657dcad099e1b9214527670e |
|
55af6a90ac8863f27b3fcaa416a0f1e4ff02fb42aa46a7274c6b76aa000aacc2 |
|
7e6b04e17ae273700cef4dc08349af949dbd4d3418159d607529ae31285e18f7 |
|
7e14ca8cb7980e85aff4038f489442eace33530fd02e2b9c382a4b6907601bee |
|
9024d98386c179a1b98a1f082b0c7487b22403d8d5eb3db6828725d14392ded |
|
c23f17b92b13464a570f737a86c0960d5106868aaa5eac2f2bac573c3314eb0f |
|
e2810cca5d4b74e0fe04591743e67da483a053a8b06f3ef4a41bdabee9c48cf7 |
|
f925d929602c9bae0a879bb54b08f5f387d908d4766506c880c5d29986320cf9 |
|
fb58c54a6d0ed24e85b213f0c487f8df05e421d7b07bd2bece3a925a855be93a |
|
ff2ae62ba88e7068fa142bbe67d7b9398e8ae737a43cf36ace1fcf809776c909 |
Archives:
|
02060a9ea0d0709e478e2fba6e9b71c1b7315356acc4f64e40802185c4f42f1c |
|
0ab2b0a2c46d14593fe900e7c9ce5370c9cfbf6927c8adb5812c797a25b7f955 |
|
1c0947258ddb608c879333c941f0738a7f279bc14630f2c8877b82b8046acf91 |
|
31591fcf677a2da2834d2cc99a00ab500918b53900318f6b19ea708eba2b38ab |
|
4064e4bb9a4254948047858301f2b75e276a878321b0cc02710e1738b42548ca |
|
424a9c85f97aa1aece9480bd658266c366a60ff1d62c31b87ddc15a1913c10e4 |
|
53b4a4359757e7f4e83929fba459677e76340cbec7e2e1588bbf70a4df7b0e97 |
|
88788208316a6cf4025dbabbef703f51d77d475dc735bf826b8d4a13bbd6a3ee |
|
8fbd374d4659efdc5b5a57ff4168236aeaab6dae4af6b92d99ac28e05f04e5c1 |
|
a0968e820bbc5e099efd55143028b1997fd728d923c19af03a1ccec34ce73d9b |
|
c80c8dd7be3ccf18e327355b880afb5a24d5a0596939458fb13319e05c4d43e9 |
|
c88453178f5f6aaab0cab2e126b0db27b25a5cfe6905914cc430f6f100b7675c |
|
e7896ccb82ae35e1ee5949b187839faab0b51221d510b25882bbe711e57c16d2 |